Hey Ninjas! 🥷
Welcome to an in-depth write-up for the “Send the Alien Back Home” CTF challenge! This series of hands-on challenges, hosted on our Selfmade Ninja Lab platform, is designed to help you practice cybersecurity skills with a focus on path traversal vulnerabilities. 🚀 These challenges provide a unique, practical learning experience for aspiring IT students exploring cloud lab training.
Getting Started with Selfmade Ninja Labs
Follow these steps to set up and access the challenge:
- Sign in to Selfmade Ninja Labs (Click here)
- New User? Create an account here.
- Activate WireGuard:
- Configure your VPN to securely connect to the labs.
- Navigate to the dashboard:
- Visit Selfmade Ninja Labs.
- On the left-side navbar, click the “My Lab” dropdown and select “Challenge Lab.”
- Search for the “Send the Alien Back Home” challenge:
- Use the search bar to locate the challenge.
- Click the challenge button to open its details.
- Start the mission:
- On the top-right corner, click “Deploy Lab” and then hit “Start Mission.”
- Your unique lab IP will be generated.
- Set up your environment:
- Use VS Code or your preferred editor to port-forward your lab IP.
- Begin exploring the challenge!

You can jump straight into the action by accessing the Send the Alien Back Home challenges on our lab website. Each challenge will walk you through various techniques for identifying, exploiting, and defending against path traversal vulnerabilities. So, buckle up and prepare for a cybersecurity adventure with Selfmade Ninja Lab’s cloud lab training! 🌟
Prerequisites
- Make sure your computer is connected to SNA Labs [Essential lab]
🚨Alert:
If you’re unfamiliar with connecting to Challenge labs, we recommend you check out our Connecting to CTF Labs Guide for essential tips and guidelines. Always approach these challenges with a responsible and ethical mindset.
Before starting the writeup, let’s clarify what path traversal vulnerability is:
Exploring Path Traversal:
Path traversal is a critical security vulnerability in web applications, where attackers can gain unauthorized access to files by exploiting inadequately sanitized user inputs. This issue arises when applications fail to properly validate or sanitize file paths provided by users, leading to potential access to sensitive areas of the server’s file system. In our ‘Send the Alien Back Home’ challenge series, you’ll get hands-on experience with this concept, where each level intensifies in complexity. Through a series of engaging challenges, you’ll learn all about path traversal vulnerabilities and how to protect against them. 🌟 Let’s embark on this educational adventure together!
Challenge 1: The Home Intel :
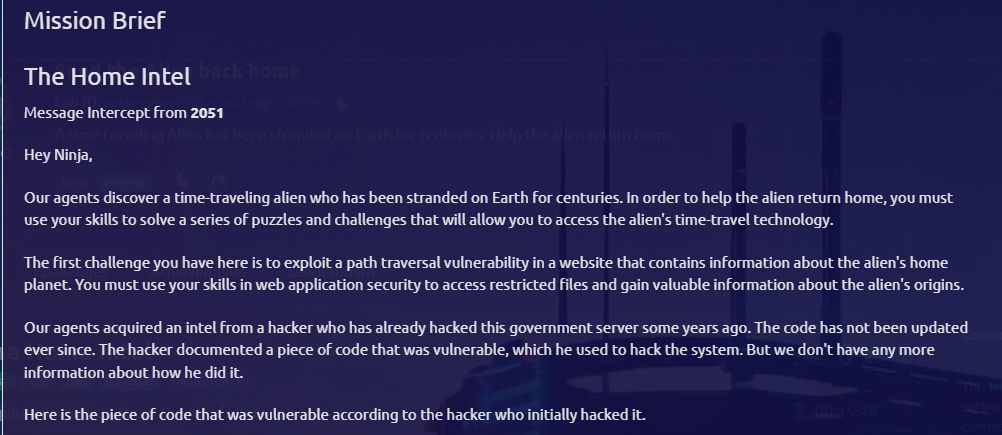
After initiating the mission, let’s first review the brief mentioned above. Pay close attention to the code within the brief as it holds key insights for our challenge.
$file_path = $_GET['file'];
function fetch_file($file_path)
{
if(file_exists($file_path))
{
$output = file_get_contents($file_path);
print $output;
}
else
{
http_response_code(404);
}
}
fetch_file($file_path);In our challenge, we’re exploring a scenario where the file parameter in a GET request is used to access files on the server. This technique can potentially expose sensitive files, depending on how the server handles these requests.
Also, take a look at the code snippet: file_get_contents($file_path);. This function is crucial, as it’s used to retrieve the contents of the specified file. 🧐
Given this information, let’s put our detective hats on 🕵️♂️ and examine the website. Remember, the brief mentioned the location of the flag. With this key piece of information, we can strategize our approach to testing the website and ultimately capture that elusive flag. 🚩 Let’s dive in and see what we can uncover!
Home page:
Payload:
Get the file mentioned in the mission brief just by entering it in the url: ?file=/documents/zoraxians_home_planet.
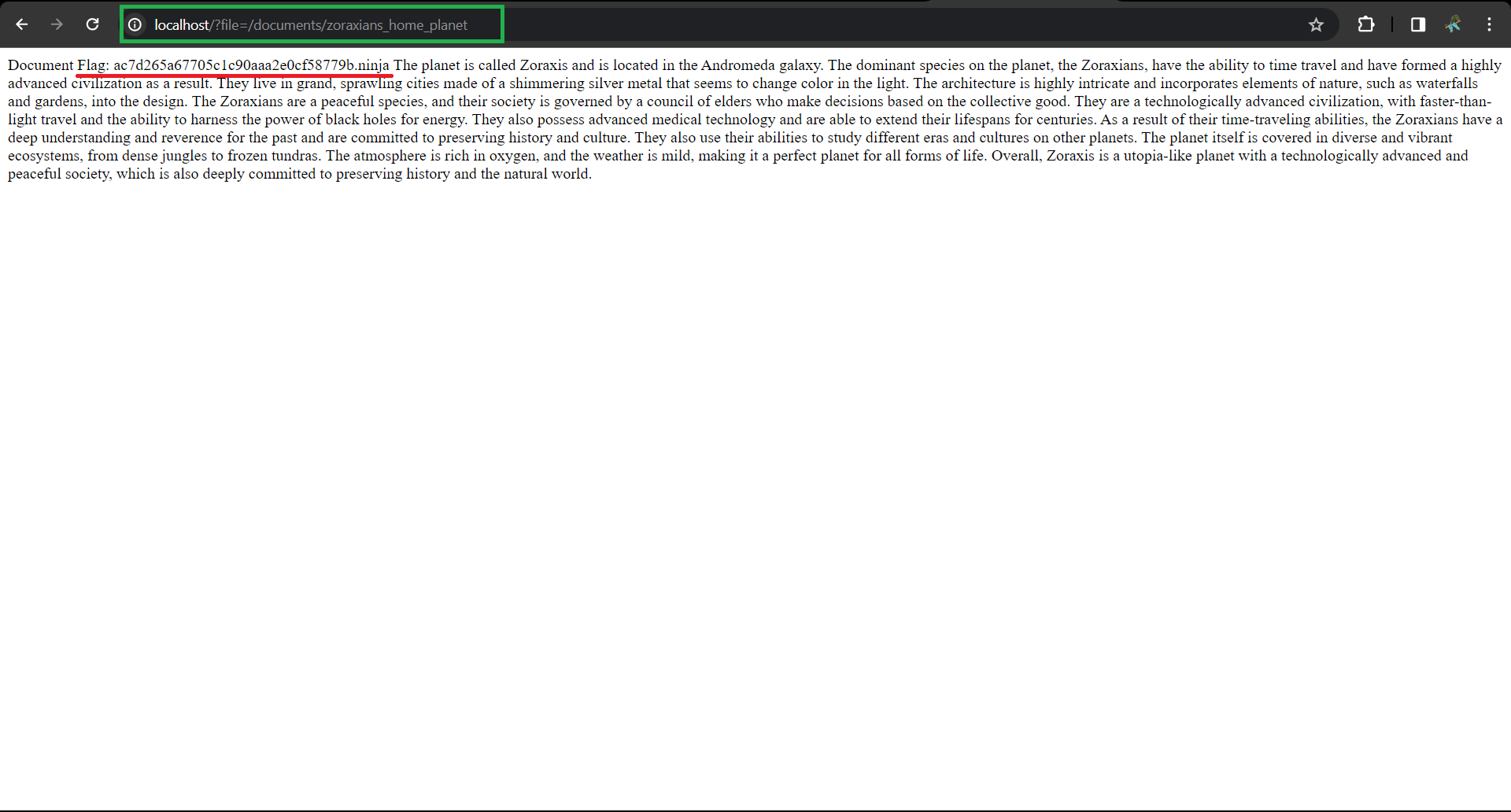
🎉 Hooray! We’ve got our first flag by passing the value of the file location of our flag /documents/zoraxians_home_planet. It turned out to be easier than expected to snag that flag, right? 😊
💡 Remember, this flag is uniquely generated for every user. Copying this flag won’t work for you. The real goal here is to practice and tackle the challenge on your own. So, get ready to dive in and learn!
Are you excited for the next challenge? Let’s keep up the momentum and move forward! 🚀
Challenge 2: The Secret Project 🗂️

Just like in our first mission, let’s kick off this challenge by delving into the mission brief. Within it, we’ve uncovered an interesting PHP code snippet:
$directory_path = "uploads/";
$file_path = $directory_path . $_GET['file'];
function fetch_file($file_path)
{
if (file_exists($file_path)) {
$output = file_get_contents($file_path);
echo $output;
} else {
echo $file_path . " " . "not found";
http_response_code(404);
}
}
Check out this key variable in the code: $directory_path = "uploads/";. It’s quite similar to what we encountered in the first challenge, involving the file parameter in a GET request and using the file_get_contents function. Plus, we’ve got a clue about the location of our flag! 🕵️ Let’s take this information and test it out on the website.
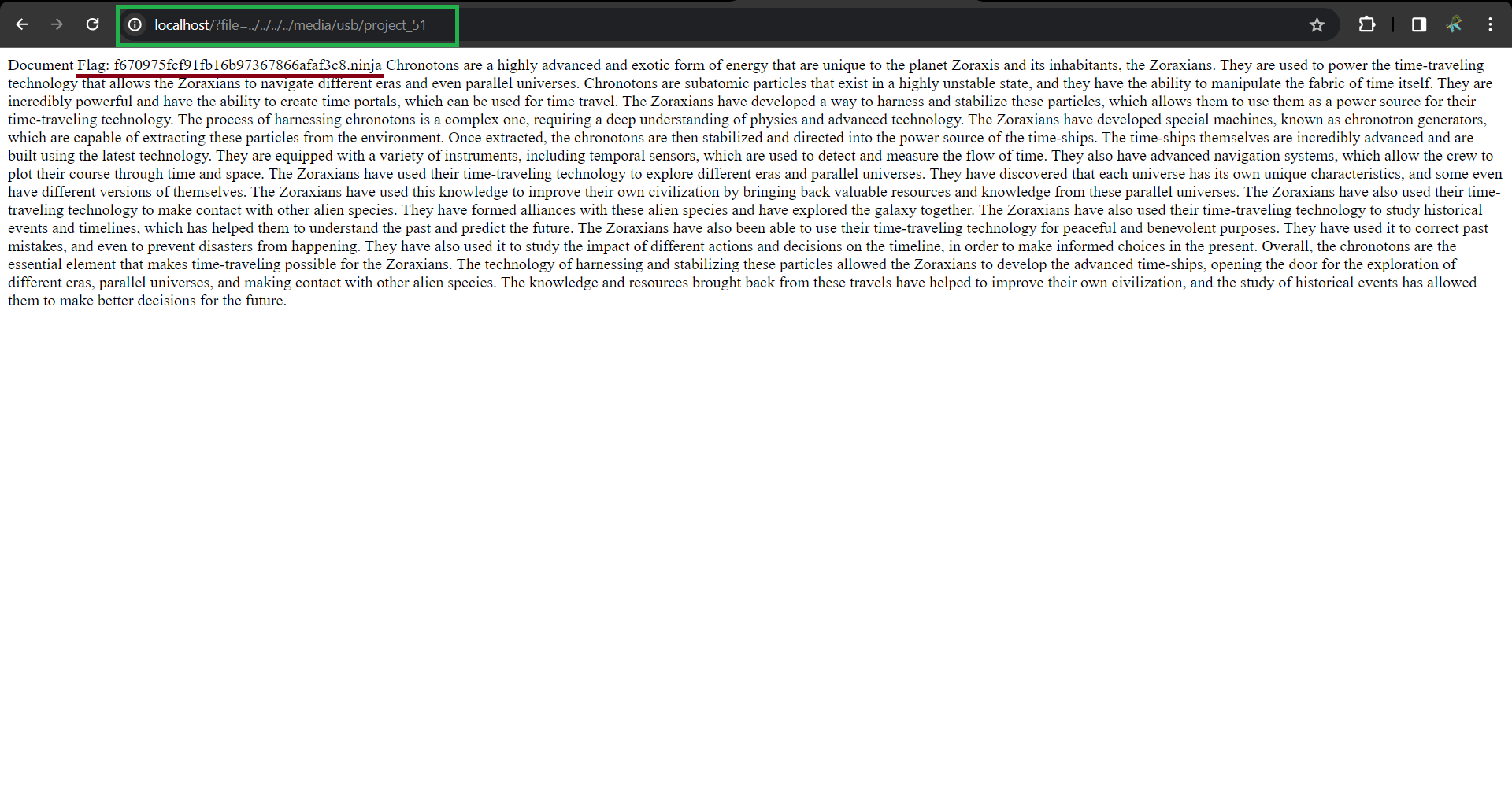
Payload:
Voila! 🎉 We’ve successfully captured the second flag, located in the ‘uploads’ directory. By cleverly navigating to file=../../../../media/usb/project_51, we uncovered it with ease. Remember, each challenge progressively becomes more intricate.🚀
Great job on the puzzles so far!, But guess what? There’s a whole bunch of new challenges coming up, and this time, you’re on your own!. There’s nothing like the feeling of solving tough puzzles on your own.
Defense Measures:
🔒 Defending against such advanced path traversal attempts is a complex task. It requires a comprehensive approach, encompassing thorough input validation, constant security protocol updates, and a deep understanding of the underlying server and application architecture. Regular security audits and penetration testing are crucial in identifying potential bypass techniques and fortifying defenses against them.
Resource:
For those keen on understanding advanced path traversal defense strategies, OWASP’s Advanced Path Traversal Guide is an excellent resource. It delves into sophisticated attack vectors and provides guidance on creating robust security frameworks to counter them.
Conclusion:
The “Send the Alien Back Home” challenge series has equipped us with essential skills for identifying and defending against path traversal vulnerabilities. This practical experience is invaluable for aspiring IT professionals in Selfmade Ninja Lab’s cloud lab training, where cybersecurity knowledge meets hands-on application. We hope this journey sparks a passion for cybersecurity and keeps you motivated for more CTF challenges. Stay tuned for new adventures, and continue honing your skills!



