Introduction
The “Security Unveiled CTF” challenge in the Yukthi CTF 2024 Finals provided an immersive experience in advanced digital forensics, credential recovery, and vulnerability exploitation. This hands-on challenge allowed participants to address real-world cybersecurity issues, offering critical skills necessary for securing privileged access in IT systems. Aspiring IT students can apply these techniques through Selfmade Ninja Lab’s cloud lab training, enhancing their practical knowledge of cybersecurity concepts.
What You Will Learn
This challenge delved into several important aspects of cybersecurity, including:
- Disk image analysis and data recovery techniques.
- Deciphering encrypted data to extract credentials.
- Conducting network scans to identify service entry points.
- Web application security testing to exploit vulnerabilities.
- Real-world application of cybersecurity concepts in a CTF context.
Challenge 1: Credential Hunt
Story
At Bout Tech, an unconventional IT company, my task was to recover the previous maintainer’s work credentials from a raw image file. This was a crucial first step to accessing the maintainer dashboard, which was pivotal for my role.
Challenge Flow
-
Disk Image Analysis: Starting with
sdb1.img, the challenge involved mounting the image and exploring its contents.sudo mkdir /mnt/image_mount sudo losetup -fP --show ./sdb1.img sudo mount /dev/loop0p1 /mnt/image_mount cd /mnt/image_mount ls -l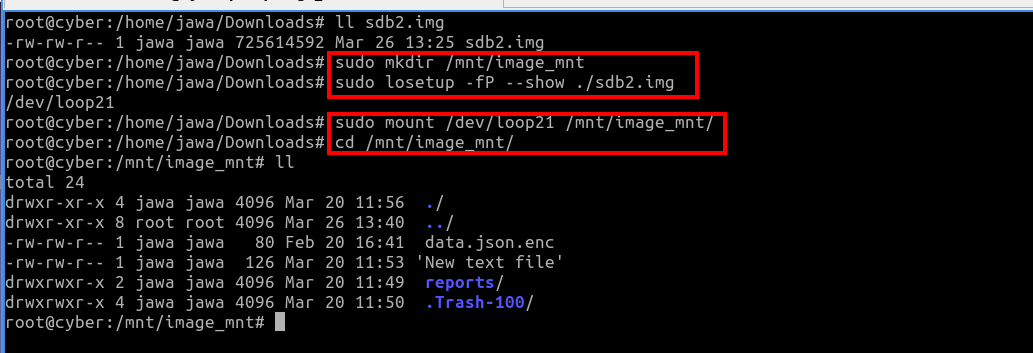
-
Decrypting Data:
Encountering
data.json.enc, a file encrypted with OpenSSL, and discovering the.Trashdirectory, which led to the crucial find ofreport.docx. After converting the DOCX to a zip and extracting,bout.jpgwas found.-
Finding report.docx:
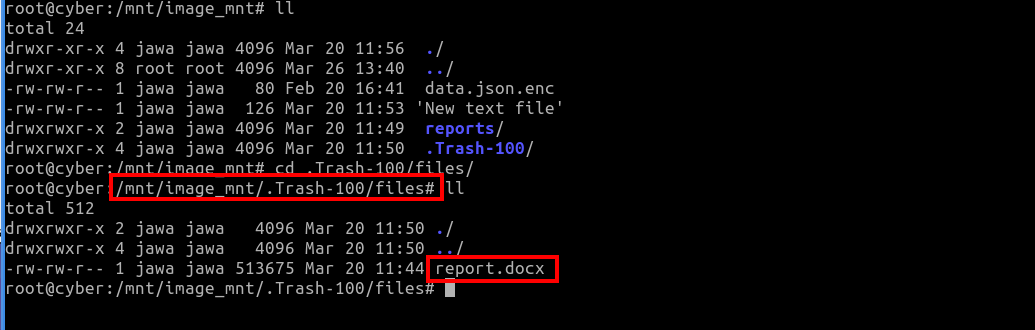
-
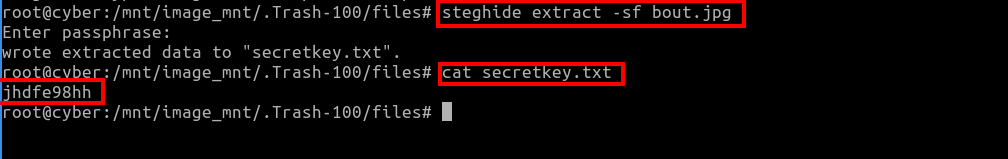
Extracting bout.jpg: Using steghide, a decryption key was retrieved from
bout.jpg.mv report.docx report.zip unzip report.zip steghide extract -sf bout.jpg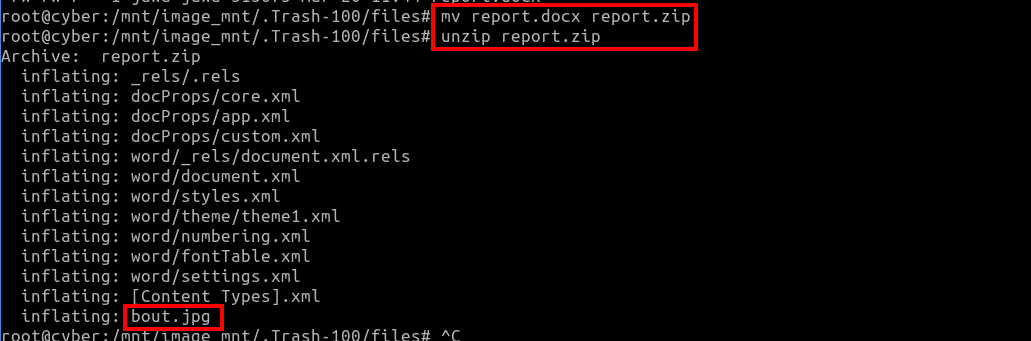
-
-
Credential Recovery: With the decryption key, the
data.json.encfile was decrypted to reveal the username and password.openssl enc -aes-256-cbc -d -in data.json.enc -out data_decrypted.json -pass pass:jhdfe98hhCredentials found:
{ "username":"clat", "location":"us", "pass":"clat@098" } -
Accessing the Dashboard: After conducting a network scan, port 80 was found to be open. The recovered credentials allowed dashboard access, revealing the first flag.
- Network Scan:
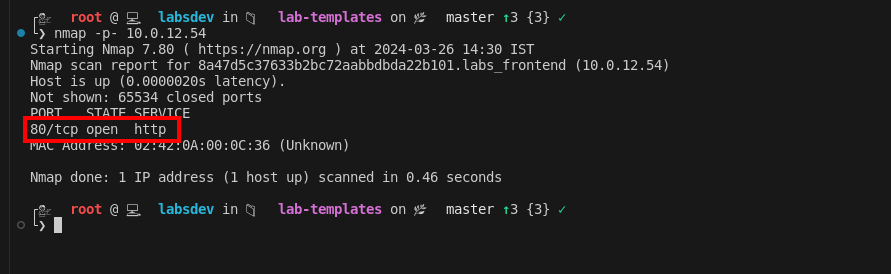
-
Dashboard Access:
After I logged in with the above credentials, I got my first flag in the dashboard section.
- Network Scan:
Challenge 2: Security Breach
Story
AAfter accessing the system, I realized admin privileges were necessary to proceed further. The website offered two login methods: one with a username and password, and another with a token sent to an email.
Challenge Flow
-
Exploring Login Methods:
The token-based login caught my interest, especially since I didn’t have the admin privileges required for deeper access.
-
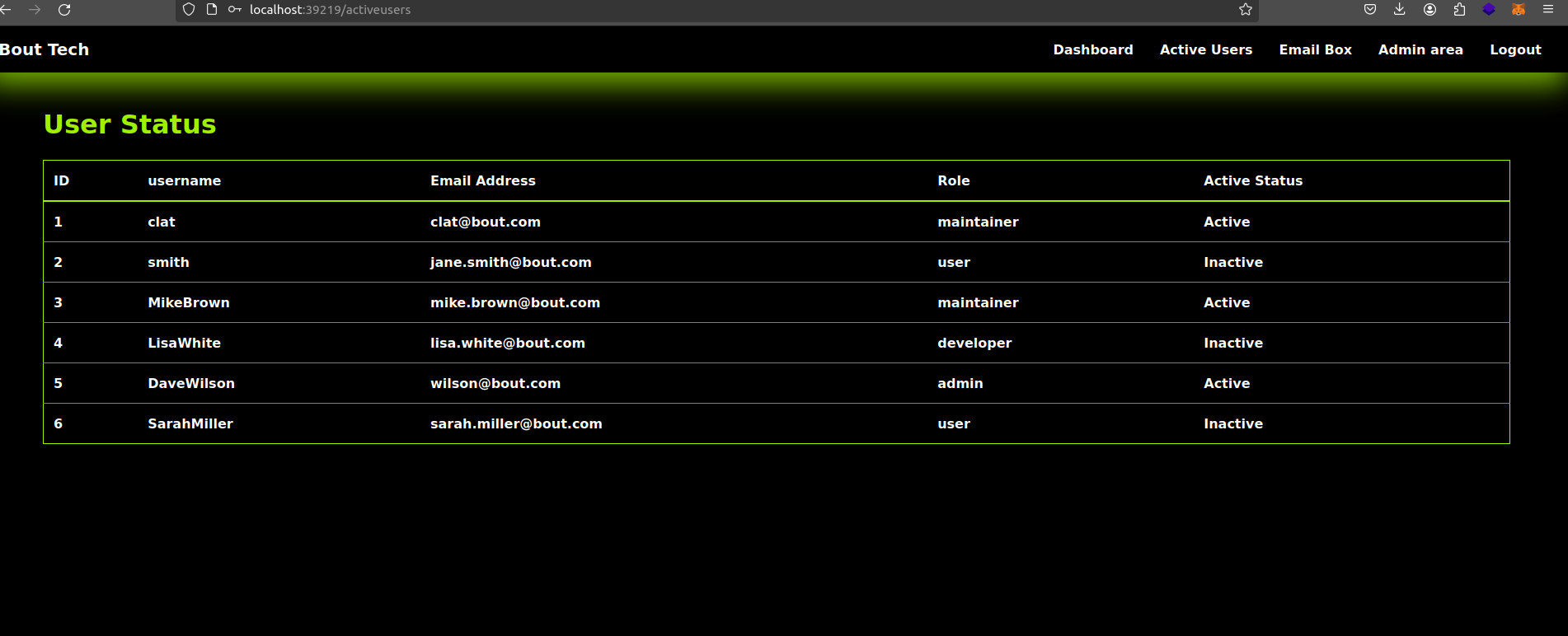
Finding an Admin User:
I found an admin email, wilson@bout.com, which seemed like a lead to gaining admin access.
-
Token System Exploit: I noticed a flaw in the token system that allowed requesting a token for both my account and the admin’s with a single submission:
wilson@bout.com&clat@bout.com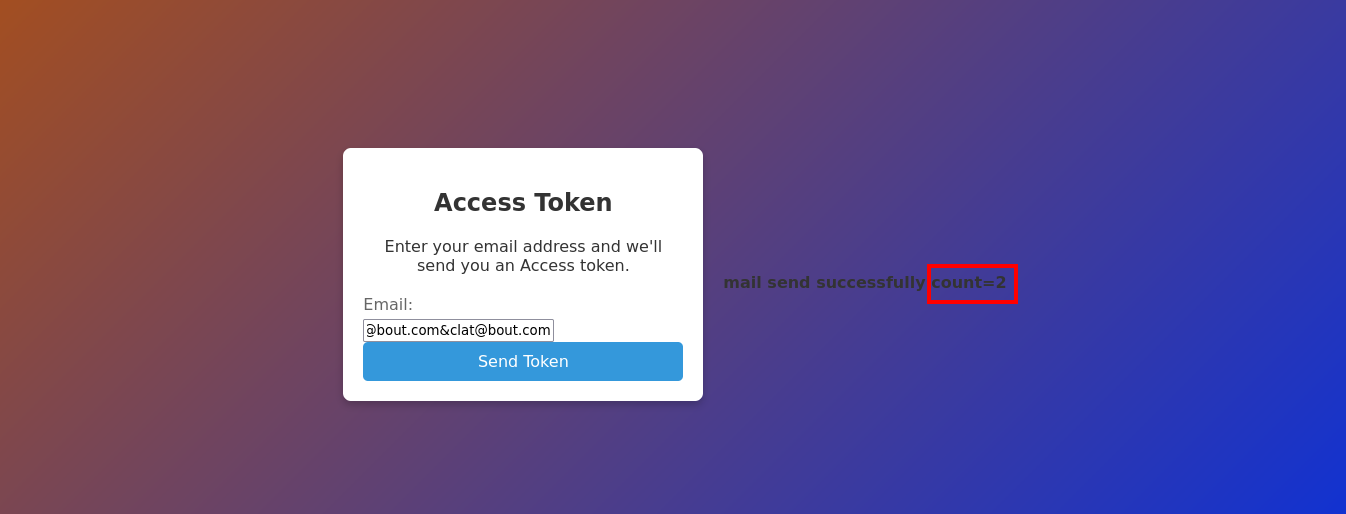
-
Receiving the Admin Token: The exploit worked, and I received an email with the admin token.
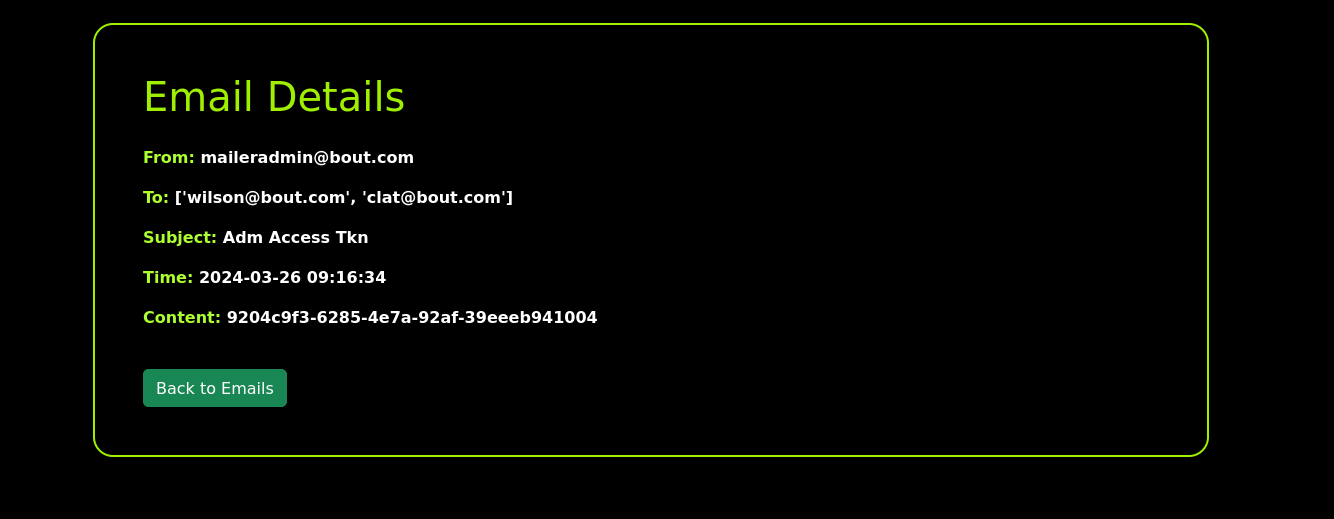
-
Admin Access Achieved:
Armed with the admin token, I proceeded to log into the admin area of the website. This crucial step allowed me to navigate the secured sections and ultimately, locate the second flag. Successfully gaining admin access not only demonstrated the vulnerability within the token system but also underscored the importance of rigorous security practices in web applications.
Conclusion
The “Security Unveiled CTF” challenge in the Yukthi CTF 2024 Finals highlighted essential cybersecurity strategies and vulnerabilities. By participating in challenges like this, students can develop practical skills in areas such as digital forensics, credential recovery, and web application security.
Through Selfmade Ninja Lab’s cloud lab training, aspiring IT professionals can gain hands-on experience and prepare for real-world cybersecurity challenges. This CTF was not just a test of technical expertise but also a demonstration of how vulnerabilities can be exploited to secure systems more effectively.



